There is a simple reason why hospitals are the frequent targets of cybercriminals. Hospital networks contain patients’ and research data that is highly valued on the black market. And their infrastructure specifics make protecting it difficult.
In 2020, all 16 Czech key hospitals covered that year by the Cybersecurity Act reported a cyber incident. But also smaller healthcare facilities were being attacked and protecting them was no less complicated.
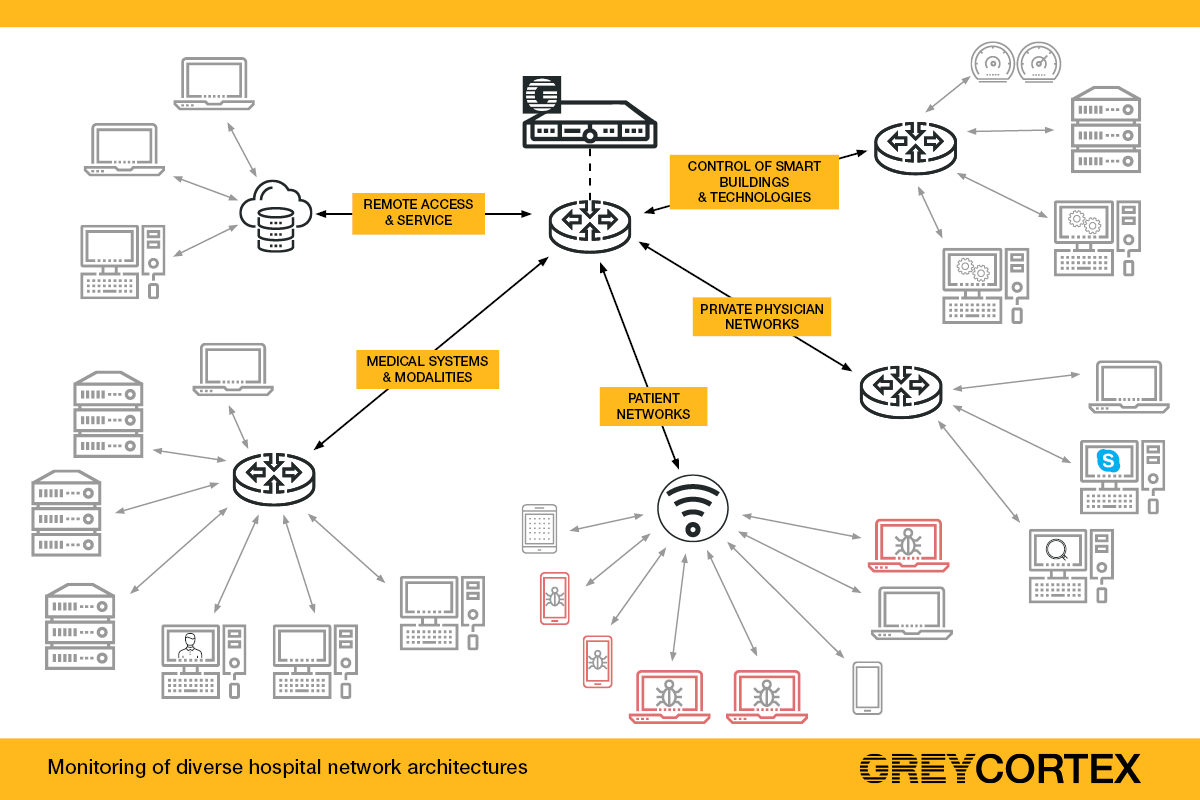
There are a few complications that make hospital cybersecurity challenging: the complex architecture of hospital networks, the frequent obsolescence of operating systems and also the insufficient number of qualified security personnel.
In addition, legislative requirements place high demands on security, including:
- GDPR
- Your National eHealth Center’s methodological guidelines (if you have one)
- International standards that summarize security recommendations for the use of healthcare systems and best practices (ENISA – Cyber security and resilience for Smart Hospitals, MDISS – Medical Device Innovation, Safety & Security Consortium)
Last, but not least, every organization usually has its own internal security regulations. These are based on risk analyses or the internal recommendations and requirements of the hospital’s governing board for the operation of IT in the hospital.
The Most Common Targets of Attackers
In the first stages, attackers aim usually at hospital employees’ login credentials, through which attackers try to gain access to VPNs, internal or health information systems. All these systems contain high-value data through which the attacker can hold the hospital to ransom.
Another source of income for attackers is research data that can be effectively monetized, but patient data is an especially big gain. The price for this information (data about a person and their health status) is from tens to hundreds of dollars per record on the black market. By contrast, mere contact details (for example, from a hacked e‑shop) are only worth units of dollars.
And, of course, there are attacks whose primary goal is to take a hospital out of operation. In the case of compromised information systems, hospitals are unable to retrieve medical records or determine the availability of drugs and supplies. In the worst case scenario, the attack affects the operational infrastructure.
In short: the hospital cannot provide the healthcare function essential for its patients.
The Specifics of Internal Hospital Networks
Hospital internal networks have a specific and rather complicated architecture. They are the combination of not only IT elements but also include the operational technology of specialized medical departments as well as devices such as air conditioning, heating or blind controls.
There are many different types of IT networks in hospitals, for example:
- Medical networks, in which doctors and nurses access medical records, inventories and other medical information
- Patient networks, which are used by patients and visitors to the hospital
- Private physician networks, which lease connectivity from the hospital and also have access to the internal network of information systems
All of this is often complicated by the frequent use of outdated systems and insufficient staff capacity to ensure the organization’s cybersecurity.
We should view these characteristics as specifics that cannot be immediately addressed but need to be kept in mind when securing health facilities. For example, some modalities (diagnostic equipment such as X‑ray machines, ultrasound, etc.) were purchased by hospitals 10 to 15 years ago and their level of security corresponds to their age. Often, the manufacturer does not even provide necessary updates, so there are devices with an un-updated operating system in the network. We have seen devices running on Windows XP. Even DOS and old versions of Linux are not rare as without these operating systems, it is not possible to use these devices.
Our experience, coming from dozens of hospitals in the European Union and Asia, has shown us that there are many hospitals with a high level of cyber protection. Unfortunately, there are also those with a large number of security shortcomings that need to be solved. Fortunately, GREYCORTEX Mendel can help them all.
Categories
- Company News (35)
- Product News (23)
- IT/OT Security (29)