There are several basic tools for securing network infrastructure that should not be missing from any organization. Let’s take a look at the role of GREYCORTEX Mendel in all those products protecting the data and network in your company.
Antivirus software, firewalls and intrusion prevention systems (IPS) should be an integral part of any organization’s cybersecurity solution. Nowadays, however, they are often not enough. That’s where Mendel steps in.
GREYCORTEX Mendel stands on several levels:
- It is a unique tool that sees, visualizes and analyzes everything in your network – devices, access and all communications.
- It is a great extension to the functionality of standard cybersecurity tools: antivirus, firewalls and network performance monitoring. They are crucial, but there are some threats that even they cannot detect. The reason is simple: attackers are often ready for these standard systems.
Mendel Sees and Visualizes in the Context of Time and Events
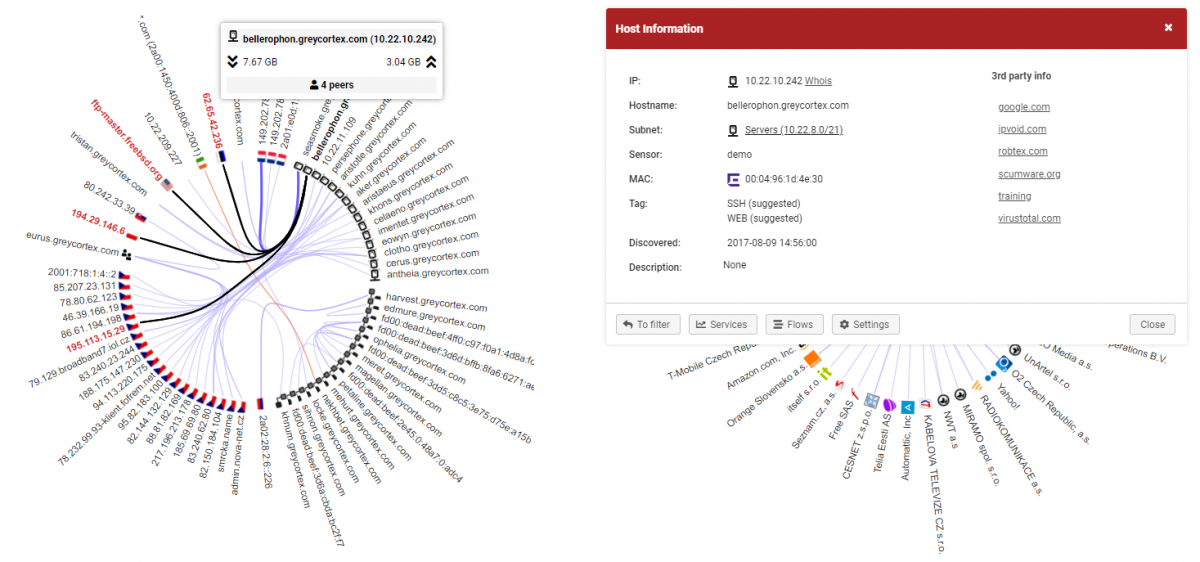
Imagine a tool that sees all the devices in your network, how they are communicating together, what protocols they are using and where your data is going. With Mendel, you can see all of that. You can also view the details of a specific device, its communication and where it is connected to at the moment, and also yesterday or a year ago.
With this unique analysis, you can uncover a sophisticated attack on your infrastructure before it really happens. That’s because you can relate current events to events that happened before, even in the more distant past.
Let’s take a look at an example of an attack that may go unnoticed by a standard detection mechanism: Advanced malware is not detected on the end device, but that device shows behavior that could endanger the network – for example, trying to access somewhere it has not accessed before. It could be spyware or an APT in your internal domains that is gradually spreading across your network through a domain, while the infected machines start accessing unusual devices and data sources and performing lateral movement. Mendel can identify and notify you of such unusual behavior.
More Reliable End-Point Security
Because end-points are an easy target, often provide valuable data and are an entry point for gaining deeper access to your network, they are the frequent initial targets of cyber-attacks.
Commonly known end-point attacks include:
- network mapping
- data exfiltration (sending data in non-standard or encrypted channels, communication with control devices)
- Dictionary attacks, password data breaches
- Data mining (reading important information, mining data from a database, mining users from information systems or from a domain controller)
Mendel flags such attacks as dangerous behavior and recognizes the threat that might not have been recognized by endpoint security or that is well hidden by the attacker. Even if antivirus software is deployed, Mendel monitors the communication of your devices and reveals any anomalies in it. All of that using a broad database specializing in network cyber threats that include not only known threats but also signatures of unusual behavior.
A Smarter Firewall
We can understand a few things that fall under the term firewall: standard firewalls and smart solutions known as an IPS.
Traditional firewalls stand first in the line of defense and secure broad traffic filtering. They adjust network transitions and the availability of network services and are mostly used on the external perimeter – in some cases within the internal network. They are often open or insufficiently configured.
In such cases, Mendel plays the role of an auditing tool – controlling the function of the firewall itself and checking its configuration. You can use this feature for verifying and controlling the communication matrix in your internal network and critical systems. It helps you understand who is connecting where, who is using what and who is behaving differently than they should.
Smart solutions such as IPS see more deeply into your network, can detect known threats and block them. Also here, Mendel provides you a double-check by monitoring the operation of web proxies and email gateways. This means no potential threat can pass. Even in this case, Mendel’s advantage is its extensive database of threats, consisting of multiple sources and signatures that verify not only known attacks but also security policies and potentially dangerous access to data sources, such as administrative sharing. This approach is much more effective for the detection of vulnerabilities than just a database of known threats from one vendor.
This way, Mendel shows much more – not only what needs to be blocked but also unwanted or insecure applications and access to risky services. You’ll get a much better overview of what is going on and what is going through your network and how.
The Danger of Unknown Threats
In all mentioned cases, Mendel not only deals better with detecting known threats, its strength lies in also detecting unknown threats. How? Mendel recognizes different types of actions using behavioral analysis.
Right after anomalous behavior or an unknown threat is detected, the system notifies you, for example, by email. It’s then your choice. You can either take the necessary steps or you can connect Mendel to the firewall API and it will block the unwanted communication automatically for you.
A Huge Help for Monitoring Network Performance
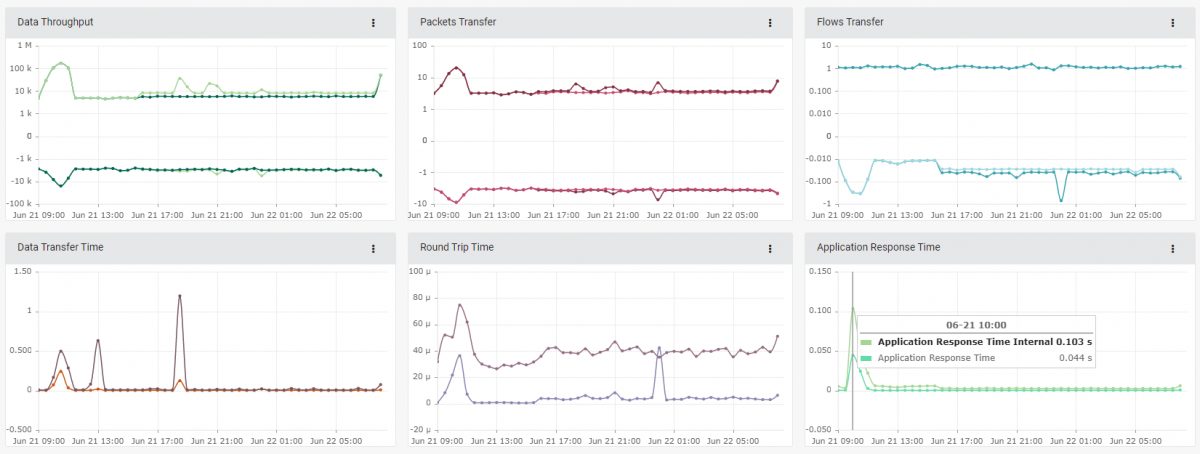
At the next level, there are tools for internal system monitoring. In this case, Mendel shows a clear overview of the network – how it is loaded and used, who is accessing it, what services are operating and what the performance of applications and transmission lines is.
Imagine seeing just how loaded your information system, domain controller, Wi-Fi network or data center are!
GREYCORTEX Mendel helps you increase the reliability of your network. Even industrial control systems can get the right amount of control, so any attack or even a major network failure has no catastrophic consequences.
Antivirus software shows you current threats. A firewall displays the current settings and whether it is leaking something or not. But nothing will clearly show you events in your network an hour, a week or a year ago. In a nutshell, Mendel sees, visualizes and (thanks to data storage of up to the last several years) also analyzes current as well as past events.
Categories
- Company News (35)
- Product News (23)
- IT/OT Security (29)